which of the following categories require a privileged access agreement
Worms and Trojan horses are types. Cyber Security Fundamentals 2020 Pre-Test This exam works as a test out function for the training and will result in a certificate upon completionYou must earn an 80 or above to pass.

Edtechsandyk Byod Equity Panel At Sxswedu 2014 Byod Teacher Classroom Equity
Which of the following categories requires a privileged access agreement.

. However the best approach for each organization is. The information security and policy provisions allow privileged access to authorized management accounts. Individuals seeking privileged access must complete and sign a PAA.
Bio Contact Client Galleries ESTD 2012She and i photographyFine Art wedding photography Thursday April 15 2021 Which Of The Following Categories Require A Privileged-Level Access Agreement If the following categories require a preferred level access agreement. They protect your emails bank accounts social media profiles and more. Leged Access Agreements PAAs regarding the responsibility of privileged users to comply with the Armys cybersecurity policy.
Many organizations have a similar path to maturity eligibility prioritizing first simple profits and the greatest risks and then gradually improving preferred security controls across the enterprise. If you own a training company youre probably always looking for new ways to increase the number of participants. Which of the following Categories Require a Privileged Access Agreement 0 All this extra privilege adds to an inflated attack surface.
Which of the following categories require a privileged access agreement. Local Admin Accounts. What is a privileged access agreement.
This answer was confirmed as. Cybersecurity is not a holistic program to manage Information Technology related security risk. Which Of The Following Categories Require A Privileged-level Access Agreement.
Which categories require a privileged access agreement. Cybersecurity is not a holistic program to manage Information Technology related security risk. Lost and found c.
Indications and precursors b. IA Technical requires a privileged-level access agreement. Routine computing for employees on personal PC users can include browsing the web streaming videos using MS Office and other basic applications including SaaS for example.
Which accounts are considered privileged accounts. Precursors and actions 2. Therefore the idea of specific categories doesnt really apply here.
IA Technical requires a privileged level access agreement. These are the most obvious accounts. Which of the following Categories Require a Privileged-Level Access Agreement.
Individuals only after they have read and signed this Agreement. February 12 2022 Uncategorized Privileged access is granted to authorized employees who may affect important files data network communications etc. 1 Answers Connor Sephton answered There can be a privileged-level access agreement for almost any sort of computer system contract document or software application.
In accordance with AR 25-2 whose responsibility is it to ensure all users receive initial and annual IA awareness training. Which of the following certifications would satisfy IAM level II and IAM level III. However you should still follow the policies and procedures.
This test can only be attempted once every 60 minutes. Privileged access enables an individual to take actions that may affect computing systems network communication or the accounts files data or processes of other users. Which of the following categories require a privileged access agreement.
Indications of an incident fall into two categories a. These accounts are typically non-personal and provide administrative access to the local host. Devices must be configured with separate accounts for privileged administrator and non-privileged user access.
You can also reduce the time you spend on administrative tasks related to training submissions to spend more time on value-added tasks. Categories and specialties within the cyberse-curity workforce that require a PAA.

Privileged Access Management Senhasegura
Configure Citrix Workspace App For Linux
Understand Admin Access And Rbac Policies On Ise Cisco

Understanding Privileged Access Management Pam Strongdm

Understanding Privileged Access Management Pam Strongdm
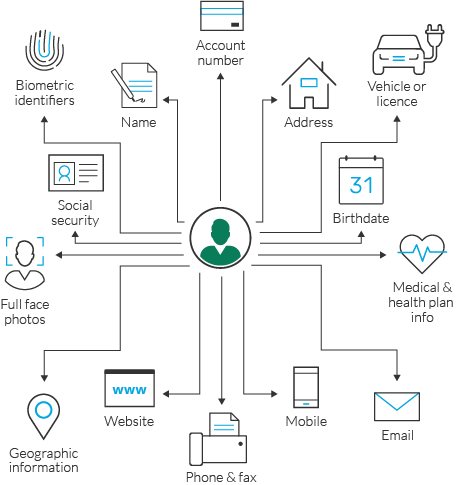
What Is Personally Identifiable Information Pii Data Security Imperva

Cybersecurity Breaches Caused By Insiders Types How To Prevent Them Ekran System
Understanding Privileged Access Management Pam Strongdm

Powerful Privileged Access Management Cloud Or On Premises

Understanding Privileged Access Management Pam Strongdm
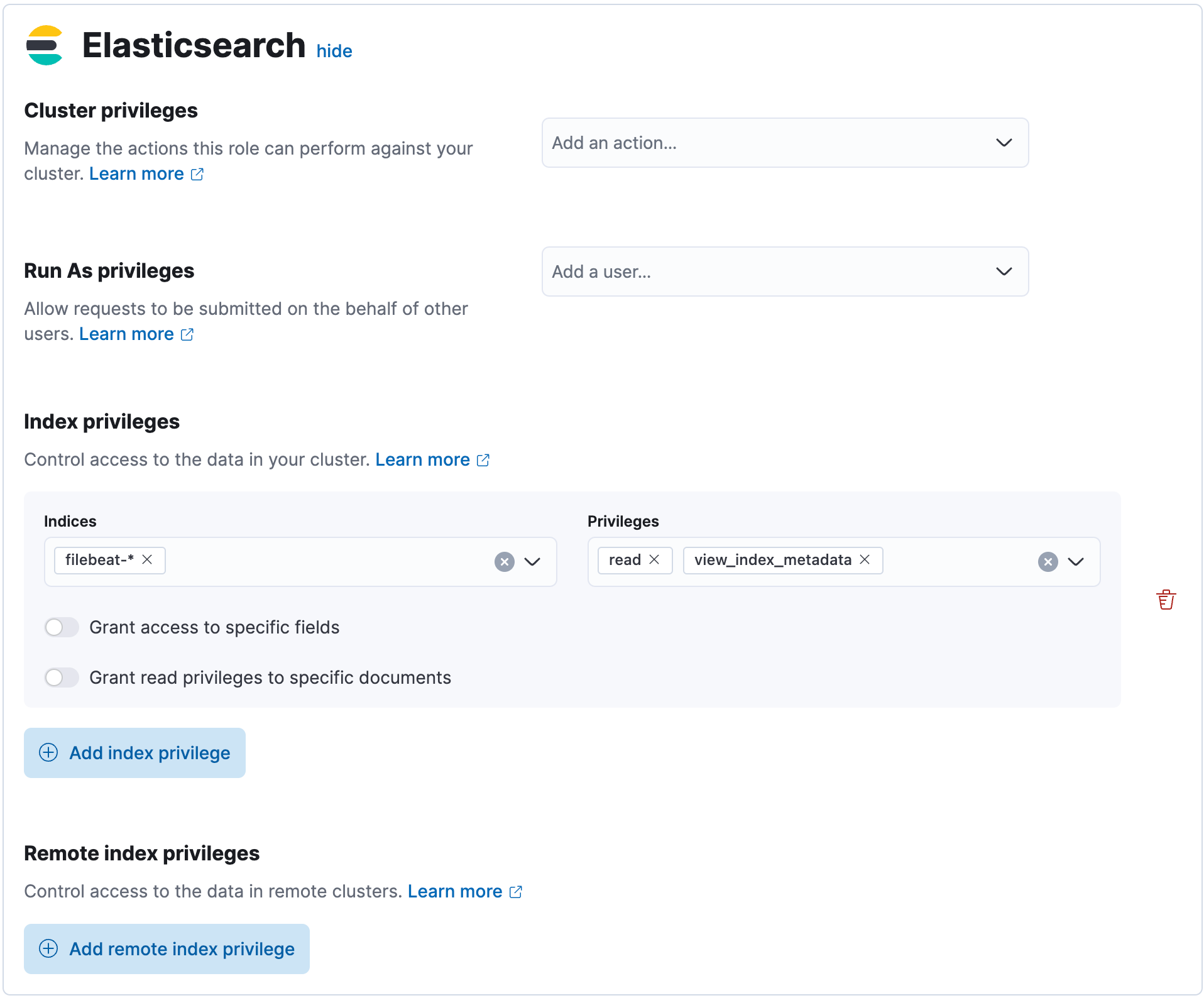
Kibana Role Management Kibana Guide 8 2 Elastic

Understanding Privileged Access Management Pam Strongdm
What Is Privileged Access Management Pam Explained Security Wiki
What Are The Different Types Of Penetration Testing Purplesec
Knowledge Base Article Service Portal

What Is Privileged Access Management Pam Explained Security Wiki
Archive Of What S New In Microsoft Defender For Cloud Microsoft Docs